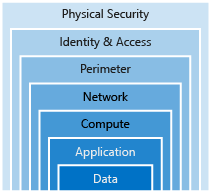
- Defense In Depth is a strategy that employs a series of mechanisms to slow the advance of an attack that is aimed at acquiring unauthorized access to information. Each layer provides protection so that if one layer is breached, a subsequent layer is already in place to prevent further exposure.
- States you should never assume trust but instead continually validate trust.
- Relies on verifiable user and device trust claims to grant access to organizational resources.
- No longer is trust assumed based on the location inside an organization' perimeter.
- Data: (Integrity) - Data encryption at rest in Azure Blob Storage
- Application: (Integrity) - SSL/TLS Encrypted Sessions
- Compute: (Availability) - Regular application of OS and layered software patches
- Network: (Confidentiality) - Network Security Rules
- Perimeter: (Availability) - DDoS Protection
- Identity & Access: (Integrity) - Azure Active Directory User Authentication
- Physical Security: (Confidentiality) - Azure Datacenter biometric access controls
Attackers are typically after data:
- In a Database
- On a Disk Inside Virtual Machines
- Stored on a SaaS app (Microsoft 365)
- Cloud Storage
Often regulatory requirements dictate the controls and processes that must be in place to ensure the confidentiality, integrity, and availability of the data.
- Ensure that applications are secure and free of vulnerabilities.
- Store sensitive application secrets in a secure storage medium.
- Make security a design requirement for all application development.
Integrating security into application development lifestyle will help reduce the number of vulnerabilities introduced in code. Encourage all development teams to make their applications secure be default. Make security requirement non-negotiable.
Secure access to virtual machines
Implement endpoint protection and keep systems patched and current.
Malware, unpatched systems, and improperly secured systems open your environment to attacks. The focus in this layer is on making sure that your compute resources are secure, and that you have the proper controls in place to minimize security issues.
Limit communication between resources through segmentation and access controls,
Deny by default.
Restrict inbound internet access and limit outbound where appropriate.
implement secure connectivity to on-premise networks.
At this layer, the focus is on limiting network connectivity across all your resources. Segment your resources and use network-level controls to restrict communication to only what is needed. By limiting this communication, you reduce the risk of lateral movement throughout your network.
Use Distributed Denial-of-Service (DDoS) protection to filter large-scale attacks before they can cause denial of service for users.
Use perimeter firewalls to identify and alert on malicious attacks against your network.
At the network perimeter, it is about protecting from network-based attacks against your resources. Identifying these attacks, eliminating their impact, and alerting on them are important to keep your network secure.
Control access to infrastructure (change control).
Use SSO and MFA
Audit event and changes
The identity and access layer is all about ensuring that identities are secure, access granted is only what's needed, and changed are logged.
Physical building security and controlling access to computing hardware within the datacenter are the first line of defense.
With physical security, the intent is to provide physical safeguards against access to assets. This ensures that other layers can't be bypassed, and that loss or theft is handled appropriately.
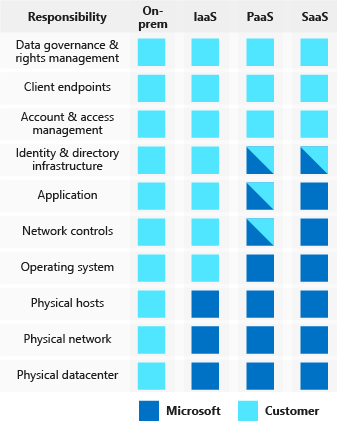
- As computing environments move from customer-controlled datacenters to cloud datacenters, the responsibility of security also shifts. Security is now a concern that both cloud providers and customers share.
The threat landscape is evolving in real time and at massive scale, so a security architecture is never complete. Microsoft and its customers need the ability to respond to these threat intelligently, quickly, and at scale.
Azure Security Center provides customers with unified security management and advanced threat protection to understand and respond to security events on-premises and in Azure. In turn, Azure customers have a responsibility to continually reevaluate and evolve their security architecture.
Digital identities are an integral part of today's business and social interactions on-premises and online. Recently mobile devices have become the primary way that people interact with digital services. This has driven the development of identity protocols that can work at internet scale across many disparate devices and operating systems.
As your organization evaluates the capabilities of its architecture around identity, it is looking at ways of bringing the following capabilities into the application:
Provide SSO to application users
Enhance the application to use modern authentication with minimal effort.
Enforce multi-factor authentication for all sign-ins outside the company's network.
Develop an application to allow patients to enroll and securely manage their account data.
- Users need to remember only one ID and Password.
- Access across applications is granted to single identity tied to a user, simplifying the security model.
- As users change roles or leave an org, access mods are tied to the single identity, greatly reducing the effort needed to change or disable accounts.
- Azure AD is a cloud-based identity service.
- Has built-in support for synchronizing with your on-prem AD instance, or it an be used on its own.
- Admins and devs can control access to data and applications by using centralized rules and policies configured in Azure AD.
- An additional paid-for offering that provides oversight of role assignments, self-service, and just-in-time (JIT) role activation.
- Azure AD PIM allows you to manage, control, and monitor access to important resources.
- Key Features of PIM:
- Providing just-in-time privileged access to Azure AD and Azure resources.
- Assigning time-bound access to resources by using start and end dates.
- Requiring approval to activate privileged roles.
- Enforcing Azure AD MFA to activate any role.
- Using justification to understand why users are activated.
- Getting notifications when privileged roles are activated.
- Conducting access reviews to ensure that users still need roles.
- Downloading an audit history for a internal or external audit.
- To use PIM, you need one of the following:
- Azure AD Premium P2
- Enterprise Mobility + Security (EMS) E5
Identity: A thing that can be authenticated. Includes usernames and passwords. Can also include applications or other servers, which might authenticate with secret keys or certs.
- A bonus definition, an Account is data associated with an identity.
Principal: An identity that acts with certain roles or claims. Consider the use of Sudo on a Bash prompt or on Windows via Run as an Administrator. In both cases you are still signed in as the same identity, but you have changed your role.
Service Principal: An identity that a service or application uses. Can be assigned roles.
- The process of making data unreadable and unusable.
- To use/read the encrypted data, it must by decrypted, which requires the use of a secret key.
- There are two top-level types of encryption:
- Symmetric
- Asymmetric